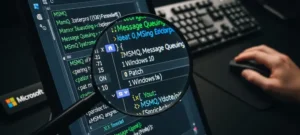
The proliferation of integrated development environments has given rise to sophisticated tools that, while boosting productivity, inadvertently create new and complex attack surfaces for threat actors. The Windows Subsystem for Linux 2 (WSL2) stands out as a prime example, offering developers a seamless Linux experience within Windows but also presenting a significant visibility gap for traditional security monitoring. The architecture