Cyber Security
- Cyber Security

Beyond the headlines of conventional warfare, a persistent and clandestine conflict is unfolding across global networks, where nations deploy sophisticated digital operatives to harvest intelligence and secure geopolitical dominance. This escalating shadow war in cyberspace poses a direct and formidable
- Cyber Security

Beyond the headlines of conventional warfare, a persistent and clandestine conflict is unfolding across global networks, where nations deploy sophisticated digital operatives to harvest intelligence and secure geopolitical dominance. This escalating shadow war in cyberspace poses a direct and formidable
Popular Stories
- Cyber Security

The cybersecurity industry’s relentless pursuit of artificial intelligence and next-generation defenses often overshadows a stark and inconvenient truth: the most damaging breaches still exploit the most elementary security gaps. In an increasingly chaotic and complex threat landscape, a significant strategic
Deeper Sections Await
- Cyber Security

The ubiquitous black-and-white squares of QR codes, once symbols of convenient access to information, have been insidiously repurposed into a potent delivery mechanism for sophisticated cyberattacks. The use of weaponized QR codes in mobile malware campaigns represents a significant evolution
- Cyber Security

A meticulously planned server update designed to fortify system defenses has instead become the source of widespread operational chaos for IT administrators grappling with unexpectedly crashing websites. This scenario, far from being hypothetical, reflects the real-world impact of a recent
Browse Different Divisions
- Cyber Security

The ubiquitous black-and-white squares of QR codes, once symbols of convenient access to information, have been insidiously repurposed into a potent delivery mechanism for sophisticated cyberattacks. The use of weaponized QR codes in mobile malware campaigns represents a significant evolution
- Cyber Security
The trust inherent in academic collaboration has been dangerously weaponized in a new wave of cyber espionage, where the intellectual capital of scholars is now the primary target for state-sponsored threat actors. A sophisticated campaign uncovered in October 2025 demonstrates
- Cyber Security
In the high-stakes world of cybersecurity, every second counts. For the analysts on the front lines in a Security Operations Center (SOC), the time between an initial alert and a final verdict is a critical window where a minor threat
- Cyber Security
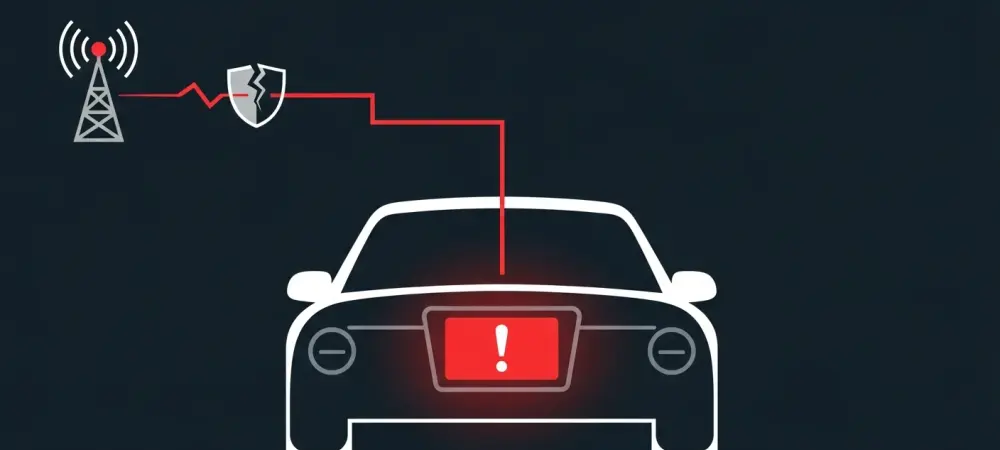
A recently uncovered security vulnerability in a widely used automotive component has transformed theoretical concerns into a tangible reality, demonstrating how hackers can remotely seize complete control of a vehicle’s dashboard infotainment system. This discovery serves as a stark reminder
- Cyber Security

A silent but potent vulnerability within the very fabric of the Windows operating system has been discovered, granting attackers the ability to seize complete control over affected systems with alarming ease. Identified as CVE-2025-55681, this high-severity flaw resides in the
- Cyber Security

A meticulously planned server update designed to fortify system defenses has instead become the source of widespread operational chaos for IT administrators grappling with unexpectedly crashing websites. This scenario, far from being hypothetical, reflects the real-world impact of a recent
Browse Different Divisions
Popular Stories
Uncover What’s Next
















