Cyber Security
- Cyber Security

Beyond the headlines of conventional warfare, a persistent and clandestine conflict is unfolding across global networks, where nations deploy sophisticated digital operatives to harvest intelligence and secure geopolitical dominance. This escalating shadow war in cyberspace poses a direct and formidable
- Cyber Security

Beyond the headlines of conventional warfare, a persistent and clandestine conflict is unfolding across global networks, where nations deploy sophisticated digital operatives to harvest intelligence and secure geopolitical dominance. This escalating shadow war in cyberspace poses a direct and formidable
Popular Stories
- Cyber Security

The cybersecurity industry’s relentless pursuit of artificial intelligence and next-generation defenses often overshadows a stark and inconvenient truth: the most damaging breaches still exploit the most elementary security gaps. In an increasingly chaotic and complex threat landscape, a significant strategic
Deeper Sections Await
- Cyber Security

The widespread integration of generative AI into corporate workflows has created a profound and often invisible crisis, leaving security leaders struggling to answer fundamental questions about their most sensitive data. As employees embrace these powerful new tools for unprecedented productivity
- Cyber Security
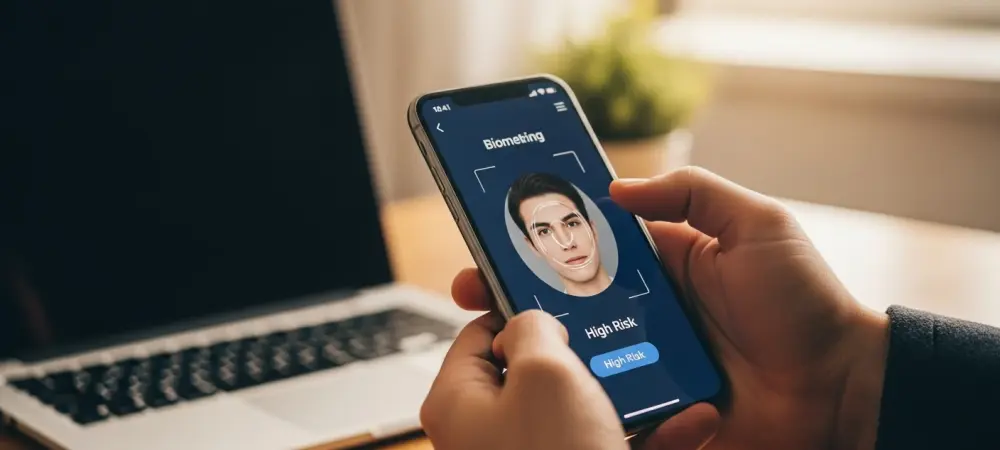
With a deep background in applying artificial intelligence and machine learning to complex security challenges, Dominic Jainy has become a leading voice in the fight against sophisticated financial fraud. As criminals increasingly turn to high-tech methods like Remote Access Trojans
Browse Different Divisions
- Cyber Security

The widespread integration of generative AI into corporate workflows has created a profound and often invisible crisis, leaving security leaders struggling to answer fundamental questions about their most sensitive data. As employees embrace these powerful new tools for unprecedented productivity
- Cyber Security

The very systems designed to provide physical security and oversight are now being scrutinized as potential gateways for sophisticated cyber intrusions, turning a watchful eye into a digital backdoor. Security researchers have recently brought to light a critical remote code
- Cyber Security

A meticulously crafted malicious extension, differing by only a single character from a trusted developer tool, can transform a secure development environment into a gateway for data exfiltration and persistent network compromise. This scenario is no longer a theoretical threat
- Cyber Security

A sophisticated piece of cyber weaponry, adaptable enough to drain a bank account or steal state secrets, is now actively circulating within the digital corridors of the Asia-Pacific region, wielded by distinct threat groups with alarmingly different motives. This development
- Cyber Security

The very fabric of corporate value is being rewoven by an invisible, persistent threat that has moved from the server room to the boardroom, fundamentally altering how companies operate, are funded, and led. By 2026, the familiar contours of business
- Cyber Security

With a deep background in applying artificial intelligence and machine learning to complex security challenges, Dominic Jainy has become a leading voice in the fight against sophisticated financial fraud. As criminals increasingly turn to high-tech methods like Remote Access Trojans
Browse Different Divisions
Popular Stories
Uncover What’s Next
















