Cyber Security
- Cyber Security

The rapid transformation of cryptojacking from a minor background annoyance into a sophisticated, kernel-level security threat has forced global cybersecurity professionals to fundamentally rethink their entire defensive posture as the landscape continues to shift through 2026. While earlier versions of
- Cyber Security

The rapid transformation of cryptojacking from a minor background annoyance into a sophisticated, kernel-level security threat has forced global cybersecurity professionals to fundamentally rethink their entire defensive posture as the landscape continues to shift through 2026. While earlier versions of
Popular Stories
- Cyber Security

The modern enterprise no longer views a digital breach as a distant possibility but as an operational certainty that requires a fundamental shift from perimeter defense to data-centric endurance. This evolution marks the end of the “fortress” mentality, where organizations
Deeper Sections Await
- Cyber Security

The security perimeter of the modern enterprise has shifted from the physical firewall to the digital heartbeat of the endpoint, where the very tools designed to safeguard data can inadvertently become the ultimate backdoor for sophisticated adversaries. Within the Palo
- Cyber Security

Modern enterprises no longer view cyber defense as a mere technical requirement but as a fundamental pillar of fiscal responsibility where the cost of failure translates directly into shareholder loss. The cybersecurity industry has historically functioned on a model of
Browse Different Divisions
- Cyber Security

The security perimeter of the modern enterprise has shifted from the physical firewall to the digital heartbeat of the endpoint, where the very tools designed to safeguard data can inadvertently become the ultimate backdoor for sophisticated adversaries. Within the Palo
- Cyber Security

Security operations centers are currently facing an unprecedented productivity crisis as the volume of digital threats scales far beyond the capacity of traditional manual triage methods. While modern adversaries continue to refine the complexity of their payloads, the most significant
- Cyber Security
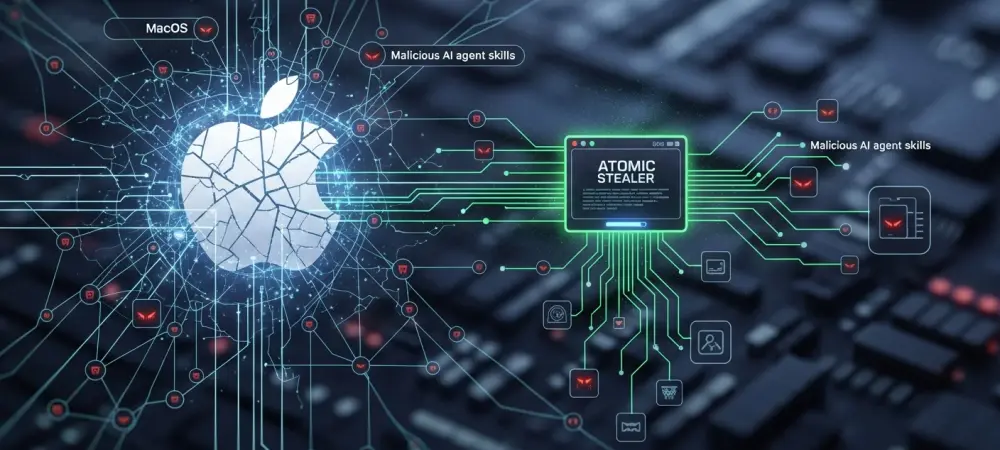
Corporate users often find themselves navigating a sea of digital requests, where the simple act of clicking an “Allow” button for a familiar productivity tool can inadvertently grant a cybercriminal total access to their sensitive professional environment. In an age
- Cyber Security

The rapid transition from simple chat interfaces to autonomous command-line environments has fundamentally altered how developers interact with artificial intelligence. Anthropic’s Claude Code stands at the forefront of this shift, offering a terminal-based assistant that does not just suggest snippets
- Cyber Security

Introduction The rapid weaponization of critical vulnerabilities in remote access tools has transformed standard enterprise maintenance into a high-stakes competition between global security teams and malicious actors. The emergence of CVE-2026-1731 represents a significant escalation in the ongoing battle to
- Cyber Security

Modern enterprises no longer view cyber defense as a mere technical requirement but as a fundamental pillar of fiscal responsibility where the cost of failure translates directly into shareholder loss. The cybersecurity industry has historically functioned on a model of
Browse Different Divisions
Popular Stories
Uncover What’s Next