Cyber Security
- Cyber Security

Beyond the headlines of conventional warfare, a persistent and clandestine conflict is unfolding across global networks, where nations deploy sophisticated digital operatives to harvest intelligence and secure geopolitical dominance. This escalating shadow war in cyberspace poses a direct and formidable
- Cyber Security

Beyond the headlines of conventional warfare, a persistent and clandestine conflict is unfolding across global networks, where nations deploy sophisticated digital operatives to harvest intelligence and secure geopolitical dominance. This escalating shadow war in cyberspace poses a direct and formidable
Popular Stories
- Cyber Security

The cybersecurity industry’s relentless pursuit of artificial intelligence and next-generation defenses often overshadows a stark and inconvenient truth: the most damaging breaches still exploit the most elementary security gaps. In an increasingly chaotic and complex threat landscape, a significant strategic
Deeper Sections Await
- Cyber Security

Unveiling a Cloud Security Crisis Imagine a scenario where a single misstep in configuration exposes the digital keys to an organization’s most sensitive data, allowing unseen attackers to infiltrate systems with ease. This is not a hypothetical nightmare but a
- Cyber Security
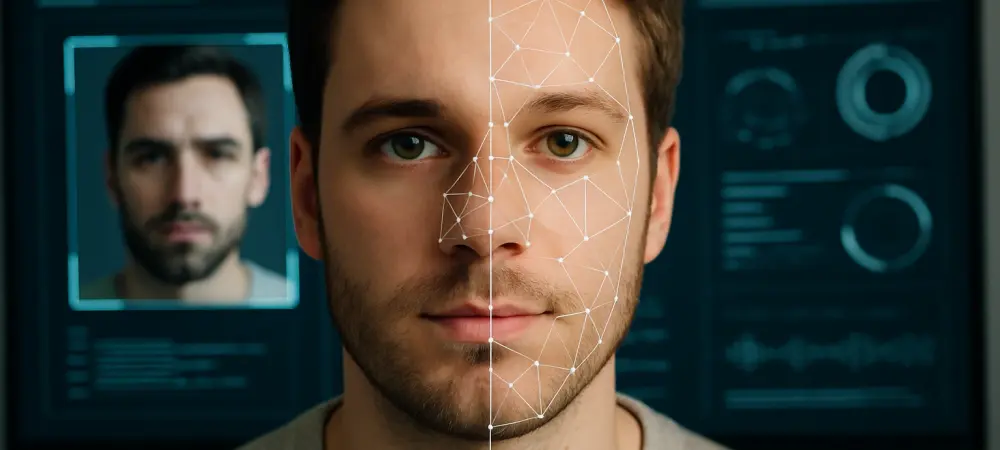
Unmasking the Threat of Synthetic Identities Imagine a scenario where a criminal seamlessly blends the facial features of two individuals into a single, synthetic image, bypassing even the most sophisticated facial recognition systems at a border checkpoint. This is not
Browse Different Divisions
- Cyber Security

Unveiling a Cloud Security Crisis Imagine a scenario where a single misstep in configuration exposes the digital keys to an organization’s most sensitive data, allowing unseen attackers to infiltrate systems with ease. This is not a hypothetical nightmare but a
- Cyber Security

Unveiling a Cybercrime Epidemic in Online Pharmaceuticals Imagine a digital marketplace where thousands of seemingly legitimate pharmacy websites promise life-saving medications at unbeatable prices, only to deliver counterfeit drugs or steal personal data. This is not a hypothetical scenario but
- Cyber Security

Setting the Stage for Cloud Security Challenges In an era where cloud-based data applications dominate enterprise operations, a staggering statistic emerges: over 80% of organizations report at least one cloud security incident annually, highlighting the fragility of digital infrastructures. A
- Cyber Security

What happens when a hidden glitch in a cloud system exposes critical data to unseen attackers, threatening years of trust and integrity? In today’s hyper-connected business landscape, where cloud platforms power operations at an unprecedented scale, such risks are no
- Cyber Security

I’m thrilled to sit down with Dominic Jainy, a renowned IT professional whose expertise in artificial intelligence, machine learning, and blockchain has positioned him as a thought leader in the tech world. With a keen interest in how emerging technologies
- Cyber Security

Unmasking the Threat of Synthetic Identities Imagine a scenario where a criminal seamlessly blends the facial features of two individuals into a single, synthetic image, bypassing even the most sophisticated facial recognition systems at a border checkpoint. This is not
Browse Different Divisions
Popular Stories
Uncover What’s Next

















