Cyber Security
- Cyber Security

Beyond the headlines of conventional warfare, a persistent and clandestine conflict is unfolding across global networks, where nations deploy sophisticated digital operatives to harvest intelligence and secure geopolitical dominance. This escalating shadow war in cyberspace poses a direct and formidable
- Cyber Security

Beyond the headlines of conventional warfare, a persistent and clandestine conflict is unfolding across global networks, where nations deploy sophisticated digital operatives to harvest intelligence and secure geopolitical dominance. This escalating shadow war in cyberspace poses a direct and formidable
Popular Stories
- Cyber Security

The cybersecurity industry’s relentless pursuit of artificial intelligence and next-generation defenses often overshadows a stark and inconvenient truth: the most damaging breaches still exploit the most elementary security gaps. In an increasingly chaotic and complex threat landscape, a significant strategic
Deeper Sections Await
- Cyber Security

Introduction to AI Cybersecurity Challenges Picture a digital fortress, housing the most cutting-edge innovations of our time, suddenly breached by invisible intruders. This isn’t a sci-fi plot but a stark reality for the AI industry, where a staggering 65% of
- Cyber Security

Imagine a giant of the automotive world, crafting luxury vehicles revered across the globe, suddenly brought to its knees—not by market forces or design flaws, but by an invisible enemy lurking in the digital shadows. In a staggering turn of
Browse Different Divisions
- Cyber Security

Introduction to AI Cybersecurity Challenges Picture a digital fortress, housing the most cutting-edge innovations of our time, suddenly breached by invisible intruders. This isn’t a sci-fi plot but a stark reality for the AI industry, where a staggering 65% of
- Cyber Security

In an era where trust is often just a click away from betrayal, a chilling wave of cyber deception has emerged, targeting those already stung by fraud. Picture this: a desperate individual, seeking justice after losing savings to an online
- Cyber Security

Imagine a quiet night shift at a sprawling manufacturing plant, where the hum of machinery suddenly grinds to a halt. A cryptic message flashes across the control room screens, demanding a hefty ransom for stolen data, while production lines stand
- Cyber Security

As the holiday season kicks into high gear, the excitement of snagging the perfect gift during Cyber Monday sales or last-minute Christmas deals often overshadows a darker reality: cybercriminals are lurking in the digital shadows, ready to exploit the frenzy.
- Cyber Security
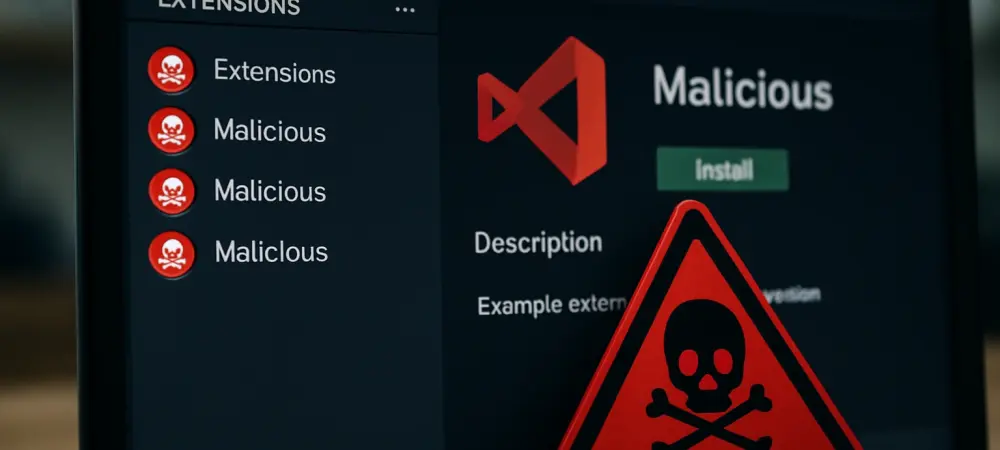
Imagine downloading a seemingly harmless code formatter for your development environment, only to discover that it’s a gateway for malware to infiltrate your system. This isn’t a far-fetched scenario but a stark reality that unfolded with the “prettier-vscode-plus” extension on
- Cyber Security

Imagine a giant of the automotive world, crafting luxury vehicles revered across the globe, suddenly brought to its knees—not by market forces or design flaws, but by an invisible enemy lurking in the digital shadows. In a staggering turn of
Browse Different Divisions
Popular Stories
Uncover What’s Next
















