In this digital age, prioritizing online security has become essential. With the release of Windows 11, Microsoft has focused on improving its security tools to provide users with a robust defense against cyber threats. This article aims to delve into the security features within Windows 11 and offer tips on further enhancing your online protection.
Windows Defender
The cornerstone of Windows 11’s security tools is Windows Defender, a free antivirus tool that comes bundled with the operating system. Over the years, Microsoft has consistently upgraded and improved Windows Defender, making it a reliable and effective solution. The continuous enhancements and regular updates ensure that it can effectively identify and remove malware, spyware, and other malicious threats, providing a strong layer of protection for your system.
Assessing Unique Requirements and Preferences
While Windows Defender offers robust protection for everyday use, some users may have unique requirements or prefer using alternative antivirus programs. If you frequently engage in risky online activities or have specific security needs, it might be worthwhile to consider additional security software. There are various reputable antivirus programs available on the market that can cater to your specific needs and preferences.
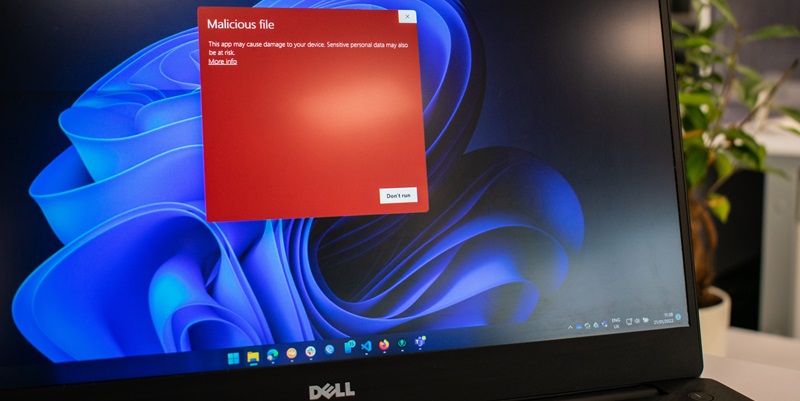
Downloading Files Safely
One of the primary ways through which malicious software can infiltrate your system is via infected files acquired through downloads. To mitigate this risk, it is crucial to only download files from trustworthy websites. Stick to reputable sources and avoid downloading files from dubious or less familiar websites. Exercise caution with “download” buttons, especially on unfamiliar sites, as they may lead to downloading potentially harmful content.
Leveraging Windows 11’s Built-in Firewall
Windows 11 comes equipped with a built-in firewall that acts as a security barrier between your computer and external networks. It is essential to keep the firewall active and properly configured to provide optimal protection. By allowing only necessary ports and applications through the firewall, you can restrict unauthorized access and minimize the risk of cyberattacks.
Using a VPN for Sensitive Online Activities
For sensitive online activities such as online banking or accessing confidential information, utilizing a Virtual Private Network (VPN) adds an extra layer of security. Although Windows 11 lacks a built-in VPN, there are numerous third-party options available that are both user-friendly and effective. These VPNs encrypt your internet traffic, ensuring that your online activities remain private and protected from prying eyes.
Importance of Regular Software Updates
Hackers continually exploit vulnerabilities in outdated software to gain unauthorized access to systems. It is imperative to keep all your software, including Windows 11, updated regularly to patch any security vulnerabilities. Regular updates address known issues and strengthen your system’s defenses, ensuring that you stay protected against the latest threats.
Protecting your online security is of paramount importance in today’s digitally connected world. Windows 11 offers a range of security tools, with Windows Defender being a dependable antivirus solution. However, depending on your requirements and preferences, additional security software may be necessary. Safely downloading files, leveraging the built-in firewall, utilizing a VPN for sensitive activities, and keeping all software updated are key practices for enhancing your online security. By prioritizing these measures, you can confidently navigate the digital landscape, knowing that you have taken proactive steps to protect yourself and your valuable data.