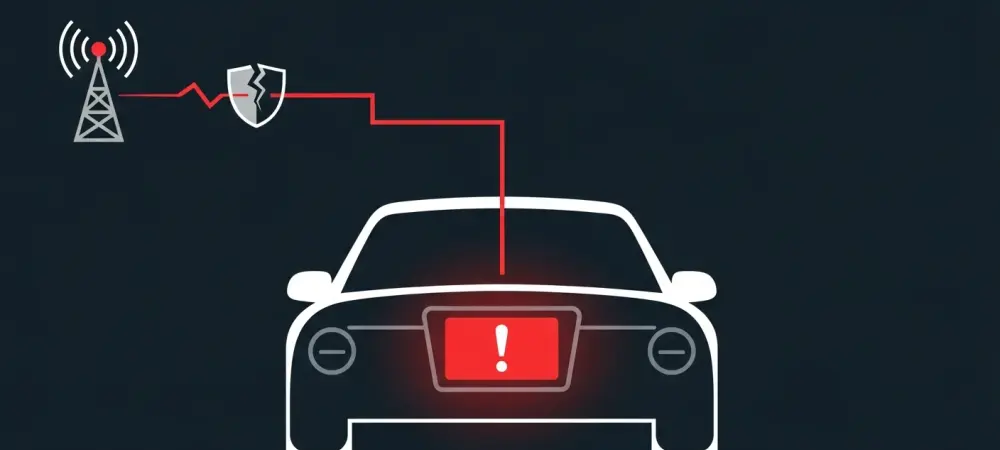
A recently uncovered security vulnerability in a widely used automotive component has transformed theoretical concerns into a tangible reality, demonstrating how hackers can remotely seize complete control of a vehicle’s dashboard infotainment system. This discovery serves as a stark reminder of the escalating security risks tied to the hyper-connectivity of modern cars, which have evolved into sophisticated Internet of Things (IoT) devices on wheels. The research presents a practical and replicable method for hijacking a vehicle’s head unit, proving that what was once a plot for a techno-thriller is now a documented and present danger. This finding highlights a critical weak point in the automotive supply chain, where a single flawed component integrated into millions of vehicles can create a widespread and severe security threat, compromising not just the system’s functionality but also the vast amounts of personal data processed by these advanced infotainment platforms.
The Anatomy of the Attack
The vulnerability’s origin lies within the Unisoc UIS7862A System-on-Chip (SoC), a component that has become popular in the automotive industry for its integrated design. This single chip houses both the application processor, which runs the dashboard’s user-facing operating system like Android, and the modem responsible for 3G, 4G, and 5G cellular connectivity. While this integration offers efficiency and cost savings for manufacturers, it also creates a critical single point of failure. The attack vector identified by security researchers uses the modem as its gateway. By remotely exploiting a deep-seated flaw in the modem’s firmware, an attacker can establish an initial foothold within the system. From this compromised position on the modem, they can then pivot laterally to the application processor, effectively bypassing security barriers and gaining ultimate control over the entire dashboard, including its screen, controls, and access to sensitive user information. This proves that isolating network components is paramount for vehicle security.
The technical foundation of this exploit is a classic yet potent stack-based buffer overflow flaw discovered within the modem’s implementation of the 3G Radio Link Control (RLC) protocol. Security analysts performing a deep dive into the firmware found that a specific function responsible for parsing incoming Service Data Units (SDUs) failed to perform adequate bounds checking. The 3G protocol specification allows a single data packet to contain a large number of optional headers. An attacker can meticulously craft a single, malformed 3G packet containing enough of these headers to overwhelm the function’s very limited stack buffer, which is a mere 0xB4 bytes in size. Critically, the developers of the firmware did not implement stack canary protection, a common security mitigation designed to detect such overflows. This oversight allows an attacker to overwrite the function’s return address on the stack, diverting the program’s execution flow to a location of their choosing and marking the first step in a complete system takeover.
From Breach to Full Control
To weaponize the buffer overflow vulnerability, researchers employed sophisticated Return-Oriented Programming (ROP) techniques. This method was necessary to circumvent modern security measures like non-executable stack protections, which prevent attackers from simply placing and running malicious code directly on the stack. Instead, ROP involves stringing together small snippets of existing code, known as “gadgets,” that are already present in the program’s memory. By carefully selecting and chaining these gadgets, an attacker can construct a ROP chain that effectively hijacks the program’s execution flow. This allowed the researchers to achieve their primary goal: executing their own arbitrary code on the modem’s processor. The successful execution of this initial payload represented the critical turning point in the attack, transforming a memory corruption bug into a powerful tool for system-wide compromise and demonstrating a high level of technical proficiency.
Once initial code execution was achieved on the modem, the attack escalated rapidly through a series of privilege-escalation steps. The attackers’ first move was to use their newfound control to patch the system’s memory protection unit, a hardware feature designed to segregate memory and prevent unauthorized access between different processes. By disabling these protections, they granted themselves write permissions across the system, effectively dissolving the digital walls separating the modem from the main application processor. This unfettered access enabled them to compromise the Android kernel, the core of the dashboard’s operating system. With the kernel under their control, the final step was trivial: they could now run any application or command on the vehicle’s head unit. This entire chain of events, originating from a single flaw in a communication module, underscored the inherent fragility of relying on integrated “black box” components within the complex and often opaque automotive supply chain.
Securing the Future of Automotive Connectivity
The discovery of this critical vulnerability served as a powerful illustration of the systemic risks embedded within the modern automotive manufacturing process. The incident revealed how the reliance on third-party, pre-packaged components like the System-on-Chip could introduce unseen and unvetted security flaws that affect millions of vehicles. It became clear that a fundamental shift was necessary in how the industry approached cybersecurity, moving beyond surface-level testing to demand deep, firmware-level security audits for every component, especially those handling external communications. This event emphasized that in an increasingly connected world, a vehicle’s security was no longer just about the strength of its physical locks but about the digital resilience of its most intricate electronic systems. The findings prompted calls for greater transparency and collaboration between automakers and their vast network of suppliers to build a more secure foundation for the future of transportation.