Cyber Security
- Cyber Security

Beyond the headlines of conventional warfare, a persistent and clandestine conflict is unfolding across global networks, where nations deploy sophisticated digital operatives to harvest intelligence and secure geopolitical dominance. This escalating shadow war in cyberspace poses a direct and formidable
- Cyber Security

Beyond the headlines of conventional warfare, a persistent and clandestine conflict is unfolding across global networks, where nations deploy sophisticated digital operatives to harvest intelligence and secure geopolitical dominance. This escalating shadow war in cyberspace poses a direct and formidable
Popular Stories
- Cyber Security

The cybersecurity industry’s relentless pursuit of artificial intelligence and next-generation defenses often overshadows a stark and inconvenient truth: the most damaging breaches still exploit the most elementary security gaps. In an increasingly chaotic and complex threat landscape, a significant strategic
Deeper Sections Await
- Cyber Security

An email alert bearing the official Instagram logo and a subject line that reads “Reset your password” can trigger an immediate spike in anxiety for any user, but when you haven’t requested it, that anxiety can quickly turn into confusion
- Cyber Security

The email that bypassed every filter and fooled the sharpest eye in finance did not originate from a human adversary, but from an algorithm designed for deception. This scenario, once the domain of science fiction, is now an operational reality
Browse Different Divisions
- Cyber Security

An email alert bearing the official Instagram logo and a subject line that reads “Reset your password” can trigger an immediate spike in anxiety for any user, but when you haven’t requested it, that anxiety can quickly turn into confusion
- Cyber Security

For countless users, the seamless consolidation of multiple email accounts into a single Gmail inbox was more than a convenience—it was the central hub of their digital communication strategy. That dependable system, however, is now a relic of the past,
- Cyber Security

The latest software update on your smartphone silently initiated a complex negotiation over your personal data, a pact between corporate giants that most users never realized they were a part of. As artificial intelligence becomes deeply woven into the fabric
- Cyber Security

An audacious claim from an Iranian-linked hacking group alleging a full compromise of Mossad communications has forced a global reevaluation of what “secure” truly means in an age of public-facing cyber-espionage. The event serves as a critical case study, with
- Cyber Security
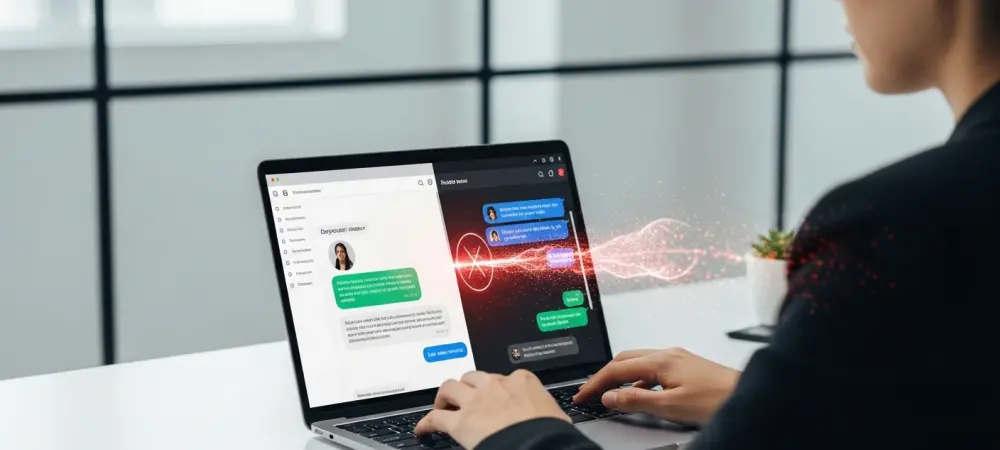
The modern digital workspace has evolved at an unprecedented pace, transforming the web browser from a simple tool for accessing information into the central hub where nearly all business-critical activities unfold. With the average knowledge worker now spending an estimated
- Cyber Security

The email that bypassed every filter and fooled the sharpest eye in finance did not originate from a human adversary, but from an algorithm designed for deception. This scenario, once the domain of science fiction, is now an operational reality
Browse Different Divisions
Popular Stories
Uncover What’s Next
















