Cyber Security
- Cyber Security

Beyond the headlines of conventional warfare, a persistent and clandestine conflict is unfolding across global networks, where nations deploy sophisticated digital operatives to harvest intelligence and secure geopolitical dominance. This escalating shadow war in cyberspace poses a direct and formidable
- Cyber Security

Beyond the headlines of conventional warfare, a persistent and clandestine conflict is unfolding across global networks, where nations deploy sophisticated digital operatives to harvest intelligence and secure geopolitical dominance. This escalating shadow war in cyberspace poses a direct and formidable
Popular Stories
- Cyber Security

The cybersecurity industry’s relentless pursuit of artificial intelligence and next-generation defenses often overshadows a stark and inconvenient truth: the most damaging breaches still exploit the most elementary security gaps. In an increasingly chaotic and complex threat landscape, a significant strategic
Deeper Sections Await
- Cyber Security

In the whirlwind of digital life, a single email can ignite a wave of panic. Recently, millions of Instagram users experienced this firsthand, deluged by a torrent of legitimate, yet unsolicited, password reset requests. The incident exposed the fragile line
- Cyber Security

Introduction The convenience of self-hosted development tools has been sharply undercut by a critical vulnerability that turns a trusted Git service into a potential gateway for system compromise. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has issued a direct
Browse Different Divisions
- Cyber Security

In the whirlwind of digital life, a single email can ignite a wave of panic. Recently, millions of Instagram users experienced this firsthand, deluged by a torrent of legitimate, yet unsolicited, password reset requests. The incident exposed the fragile line
- Cyber Security
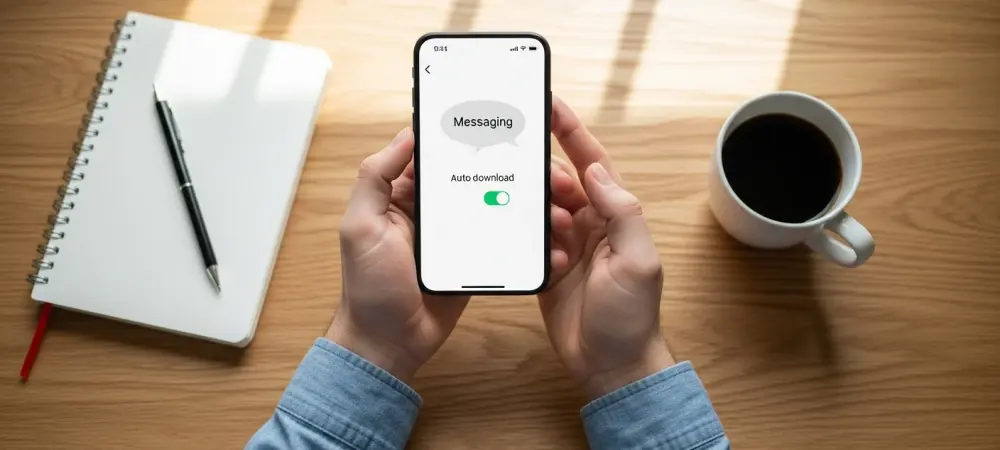
Tucked away within your smartphone’s settings is a feature most people have never heard of, yet national cybersecurity agencies are now issuing urgent warnings about its potential to create a backdoor for hackers. This seemingly innocuous setting, a relic of
- Cyber Security

As artificial intelligence agents quietly integrate into the operational backbones of corporations and critical infrastructure, a pressing and complex question has emerged that demands an immediate answer from the global technology community. The National Institute of Standards and Technology (NIST),
- Cyber Security

The very fabric of digital security is being rewoven by an artificial intelligence that acts as both the primary weapon of cyber attackers and the most sophisticated shield for defenders, creating an unprecedented and complex risk environment for organizations globally.
- Cyber Security

A single email address became the only key an attacker needed to unlock an entire enterprise’s AI infrastructure, bypassing every modern security defense in a newly discovered ServiceNow vulnerability that has now been patched. This high-severity flaw exposed the fragile
- Cyber Security

Introduction The convenience of self-hosted development tools has been sharply undercut by a critical vulnerability that turns a trusted Git service into a potential gateway for system compromise. The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has issued a direct
Browse Different Divisions
Popular Stories
Uncover What’s Next
















