Cyber Security
- Cyber Security

Beyond the headlines of conventional warfare, a persistent and clandestine conflict is unfolding across global networks, where nations deploy sophisticated digital operatives to harvest intelligence and secure geopolitical dominance. This escalating shadow war in cyberspace poses a direct and formidable
- Cyber Security

Beyond the headlines of conventional warfare, a persistent and clandestine conflict is unfolding across global networks, where nations deploy sophisticated digital operatives to harvest intelligence and secure geopolitical dominance. This escalating shadow war in cyberspace poses a direct and formidable
Popular Stories
- Cyber Security

The cybersecurity industry’s relentless pursuit of artificial intelligence and next-generation defenses often overshadows a stark and inconvenient truth: the most damaging breaches still exploit the most elementary security gaps. In an increasingly chaotic and complex threat landscape, a significant strategic
Deeper Sections Await
- Cyber Security

In an era where digital threats evolve at an alarming pace, consider a scenario where a seemingly innocuous notification on a Windows system masks a sinister operation: malware silently harvesting sensitive data and transmitting it via a trusted platform like
- Cyber Security
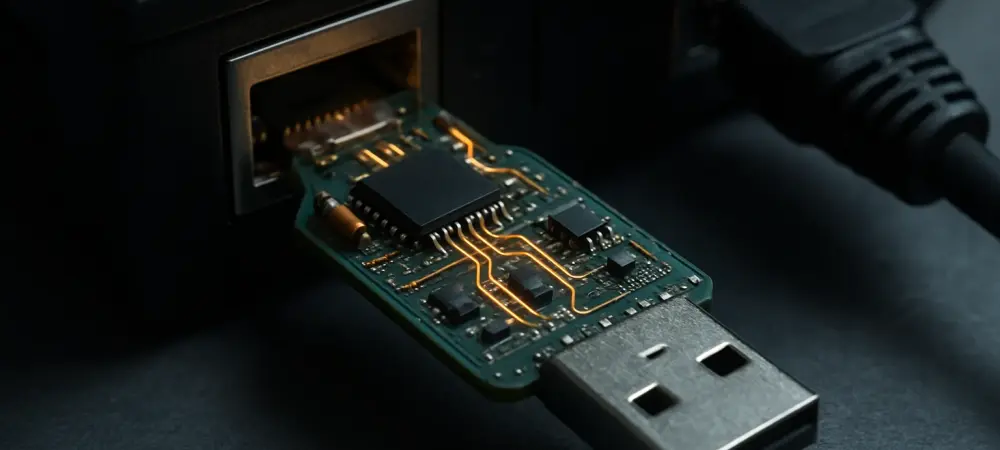
Introduction: A New Era of Cyber Stealth In an era where cyber threats evolve at an unprecedented pace, a chilling statistic emerges: over 60% of data breaches in recent years have involved sophisticated backdoors that evade traditional security measures. Among
Browse Different Divisions
- Cyber Security

In an era where digital threats evolve at an alarming pace, consider a scenario where a seemingly innocuous notification on a Windows system masks a sinister operation: malware silently harvesting sensitive data and transmitting it via a trusted platform like
- Cyber Security

Imagine a criminal network so sophisticated that it drains over $100 million from unsuspecting victims across the globe, exploiting both emotional vulnerabilities and corporate weaknesses with chilling precision. This staggering reality came to light with the extradition of four Ghanaian
- Cyber Security

Overview of Microsoft Teams and Its Global Importance Imagine a world where millions of professionals across diverse industries suddenly find their primary communication tool faltering at a critical moment, leaving them stranded in the midst of vital projects. Microsoft Teams,
- Cyber Security

This guide aims to equip individuals affected by a significant cybersecurity incident involving a major insurance provider with the tools and knowledge to safeguard their personal information. With sensitive data of approximately 1.4 million customers exposed, totaling nearly 2.8 million
- Cyber Security

What if the digital threats lurking in every download, email, or update could outsmart even the best human defenses? In an era where malware evolves at breakneck speed, costing billions in damages annually, the cybersecurity landscape faces an unprecedented challenge
- Cyber Security

Introduction: A New Era of Cyber Stealth In an era where cyber threats evolve at an unprecedented pace, a chilling statistic emerges: over 60% of data breaches in recent years have involved sophisticated backdoors that evade traditional security measures. Among
Browse Different Divisions
Popular Stories
Uncover What’s Next
















