Cyber Security
- Cyber Security

Beyond the headlines of conventional warfare, a persistent and clandestine conflict is unfolding across global networks, where nations deploy sophisticated digital operatives to harvest intelligence and secure geopolitical dominance. This escalating shadow war in cyberspace poses a direct and formidable
- Cyber Security

Beyond the headlines of conventional warfare, a persistent and clandestine conflict is unfolding across global networks, where nations deploy sophisticated digital operatives to harvest intelligence and secure geopolitical dominance. This escalating shadow war in cyberspace poses a direct and formidable
Popular Stories
- Cyber Security

The cybersecurity industry’s relentless pursuit of artificial intelligence and next-generation defenses often overshadows a stark and inconvenient truth: the most damaging breaches still exploit the most elementary security gaps. In an increasingly chaotic and complex threat landscape, a significant strategic
Deeper Sections Await
- Cyber Security

A critical vulnerability discovered in the widely used SmarterMail email server software has exposed organizations to complete server takeovers by unauthenticated attackers, bypassing all security controls with alarming simplicity. This flaw, tracked as CVE-2026-23760, allows a malicious actor without any
- Cyber Security

The humble inbox, once a simple digital mailbox, is undergoing its most significant transformation in years, prompting a wave of anxiety throughout the email marketing community. With Google’s integration of its powerful Gemini AI model into Gmail, features that summarize
Browse Different Divisions
- Cyber Security

A critical vulnerability discovered in the widely used SmarterMail email server software has exposed organizations to complete server takeovers by unauthenticated attackers, bypassing all security controls with alarming simplicity. This flaw, tracked as CVE-2026-23760, allows a malicious actor without any
- Cyber Security

With a deep background in artificial intelligence and blockchain, Dominic Jainy has a unique vantage point on the evolving threats facing modern technology sectors. He joins us today to dissect the ‘Contagious Interview’ campaign, a sophisticated operation that has turned
- Cyber Security

The growing integration of artificial intelligence into critical workflows has quietly introduced a new and formidable class of security risks, as recent research demonstrates how manipulating an AI’s conversational input can lead to a full-scale compromise of its underlying server
- Cyber Security

Today we’re joined by Dominic Jainy, an IT professional whose expertise spans the complex worlds of artificial intelligence, machine learning, and blockchain. With a keen eye for how these technologies shape our digital lives, Dominic offers a unique perspective on
- Cyber Security
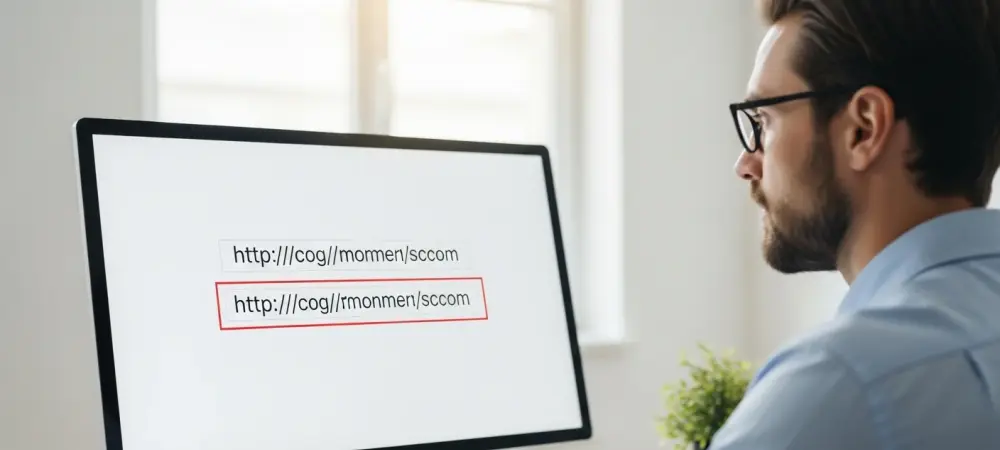
The most effective digital threats are often the ones you never see coming, hiding in plain sight within a web address that looks almost perfect, and the threat of phishing represents a significant and growing challenge in the cybersecurity sector.
- Cyber Security

The humble inbox, once a simple digital mailbox, is undergoing its most significant transformation in years, prompting a wave of anxiety throughout the email marketing community. With Google’s integration of its powerful Gemini AI model into Gmail, features that summarize
Browse Different Divisions
Popular Stories
Uncover What’s Next
















