That moment of technological frustration during a critical video conference when your camera fails or audio cuts out is a near-universal experience in the modern workplace, a vulnerability threat actors are now skillfully weaponizing. This common annoyance has become the linchpin for “ClickFix,” a novel social engineering technique that transforms an organization’s own employees into unwitting accomplices in malware delivery. The significance of this vector lies in its ability to manipulate users into manually executing malicious code, bypassing traditional security measures. This analysis dissects the ClickFix mechanism, examines its evolution through a recent and highly deceptive campaign, and outlines critical defensive strategies for the modern enterprise.
The Anatomy of a ClickFix Attack
From Generic Alerts to Targeted Impersonation
The ascent of social engineering frameworks like ClickFix and its related cluster, ClearFake, marked a significant shift in threat delivery throughout 2024. These campaigns have demonstrated a clear and concerning growth trend, moving away from broad, generic lures toward highly specific and convincing impersonations.
Early iterations of this technique relied on impersonating common system alerts, such as fake browser update notifications or fabricated Microsoft Word errors. However, threat actors have since refined their approach, recognizing that targeted branding yields a higher success rate. The current trend involves meticulously cloning the interfaces of legitimate corporate applications, creating a scenario where the user’s instinct to resolve a technical issue is turned against them. Statistics show a steady increase in attacks that depend on this form of manual user interaction, as it proves effective at circumventing automated defenses.
Case Study The Deceptive Google Meet Campaign
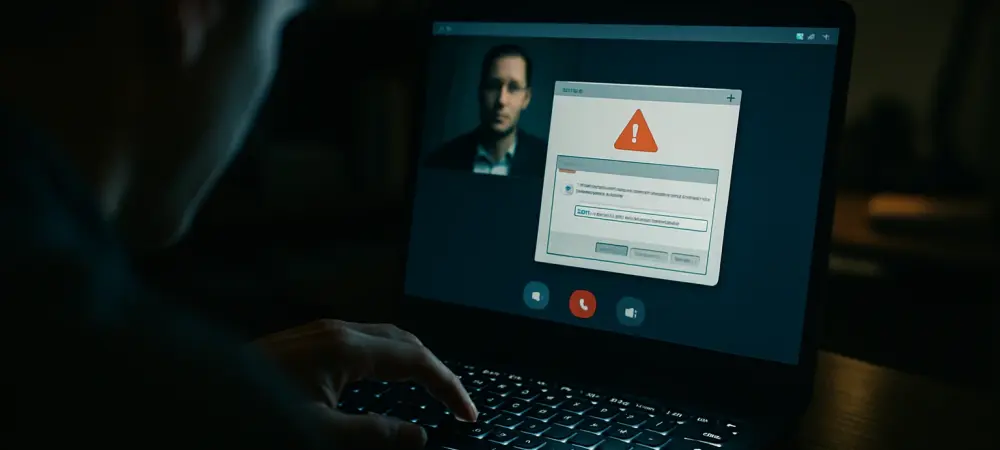
A prime example of this evolution is the recent campaign utilizing the domain gogl-meet[.]com. This attack begins when a user navigates to the fraudulent site, which presents a visually indistinguishable replica of the Google Meet interface. This high-fidelity impersonation is crucial for establishing immediate trust and lowering the user’s guard.
The core of the social engineering lure is a fake error message, often titled “Can’t join the meeting,” which interrupts the user’s attempt to start a call. Instead of requesting credentials, the site offers a technical “fix” to the problem. The user is prompted to click a “Fix” button, an action that covertly copies a malicious PowerShell script to their system’s clipboard. The on-screen instructions then guide the user to complete the attack chain by pressing the Windows key + R to open the Run dialog, pasting the clipboard contents with CTRL + V, and executing the script by hitting Enter.
Technical Analysis and Evasion Techniques
Bypassing Modern Browser Defenses
The manual execution of clipboard content is the key to this attack’s success in evading security controls. By persuading the user to run the PowerShell script via the Windows Run dialog, the threat actor shifts the execution context entirely outside of the browser’s protected environment. This simple but effective trick renders standard defenses like Google Safe Browsing and Microsoft Defender SmartScreen ineffective, as these tools are designed to inspect file downloads and malicious web traffic, not commands manually run by the user.
In contrast to traditional malware delivery through drive-by downloads or malicious email attachments, the ClickFix method places the final, critical action in the hands of the victim. This makes attribution and detection more difficult for automated systems, as there is no suspicious file download to flag. The initial website may appear benign to scanners, with the malicious payload only activated through a sequence of trusted user actions.
Payload Obfuscation and Forensic Traces
Threat actors have further refined this technique by employing advanced obfuscation in the PowerShell payload. To create a false sense of security, the malicious script is often padded with extensive comment blocks containing seemingly harmless characters, such as green check mark (✅) symbols. When the user pastes the script into the small Run dialog box, these symbols are often the only visible text, visually reassuring the victim that the command is safe or verified.
Despite these evasion tactics, the attack leaves behind critical forensic evidence. A detailed analysis of the Master File Table (MFT) on a compromised system can definitively link the resulting Remote Access Trojan (RAT) back to the attack’s origin. The MFT’s Alternative Data Stream (ADS) often contains metadata, including the referrer URL (gogl-meet[.]com), providing incident responders with an invaluable artifact to trace the infection back to the browser-based social engineering event.
Future Implications and Defensive Posture
The Evolving Landscape of Interaction Based Threats
The success of the Google Meet campaign suggests that this is only the beginning for interaction-based threats. It is highly probable that threat actors will expand their impersonation targets to include other widely used enterprise platforms such as Microsoft Teams, Slack, and Zoom. Each of these tools represents a new opportunity to exploit the commonality of technical glitches in a corporate setting.
This trend poses a significant challenge to corporate security, particularly in remote and hybrid work environments where employees are often expected to perform basic troubleshooting themselves. The line between a legitimate support instruction and a malicious command becomes dangerously blurred, making it harder for non-technical users to identify an attack. This creates a growing need for security strategies that account for the human element as the final execution vector.
Mitigation and Building Resilience
To counter this threat, security teams must adapt their detection strategies. Actionable steps include creating specific detection rules to flag PowerShell execution originating from the Run dialog, especially when the command contains unusual Unicode characters or extensive comment blocks. Monitoring for this specific behavior can provide an early warning of a successful ClickFix attack.
For end-users, the guidance must be unequivocal: any instruction from a website that requires manually running commands or scripts should be treated with extreme suspicion. Legitimate troubleshooting rarely, if ever, involves copying and pasting code from a web page into a system-level command prompt. This simple principle is a powerful defense against this entire class of attack. Ultimately, building resilience requires continuous security awareness training that moves beyond traditional phishing and focuses on these novel, hands-on social engineering tactics.
Conclusion Adapting to the New Threat Frontier
The emergence of the ClickFix technique represented a sophisticated evolution in social engineering, effectively weaponizing user trust and interaction to bypass standard security controls and deliver malware. This method marked a significant pivot from passive attacks like credential phishing toward active, user-assisted code execution. The success of campaigns targeting platforms like Google Meet underscored the threat’s viability in corporate environments. Organizations were compelled to recognize this paradigm shift and bolster both their technical detection capabilities and their human-centric defenses to counter this insidious attack vector.