The unseen digital dangers lurking in public charging ports and seemingly innocent websites have prompted a major security overhaul from Apple. The latest iOS security update represents a significant advancement in mobile device protection. This review will explore the evolution of iOS security, its key features, performance metrics, and the impact it has had on user privacy and data safety. The purpose of this review is to provide a thorough understanding of the new update, its current capabilities, and its potential future development.
The Evolving Threat Landscape for iOS
The security challenges facing iPhone users are evolving beyond traditional malware. New threats like state-sponsored spyware and physical “juice jacking” exploit common user behaviors and physical ports, creating vulnerabilities in otherwise secure environments.
While iOS is built on a strong foundation with its Secure Enclave, the threat landscape’s dynamism requires constant software evolution. Timely updates are therefore the primary defense against these sophisticated new attack vectors that target both software and hardware interfaces.
Analysis of Key Security Enhancements
Fortifying Against Physical Port Hacking
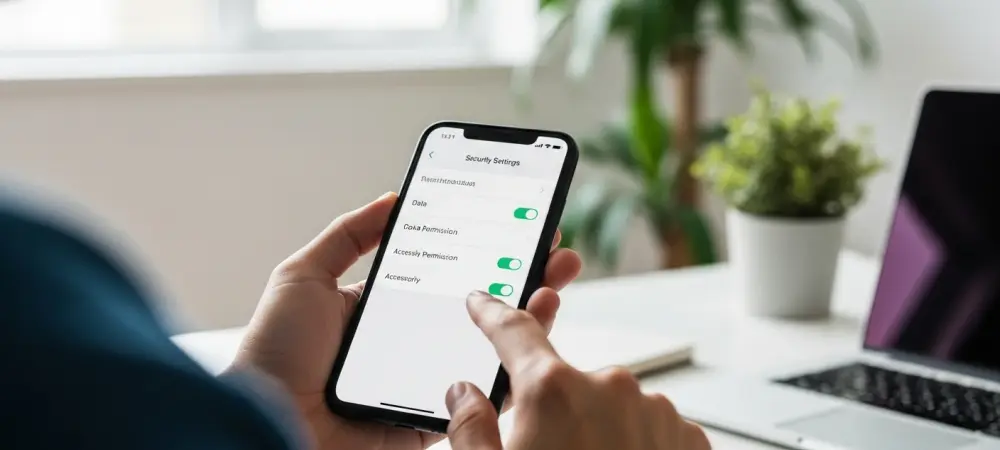
A new “Wired Accessories” setting directly combats “juice jacking” by requiring user approval before allowing a data connection via the USB-C port. By selecting options like “Always Ask” or “Ask for New Accessories,” users can effectively prevent unauthorized data access from malicious public chargers.
This feature is especially vital for travelers, directly addressing warnings from agencies like the TSA about using public charging stations. It turns a potential vulnerability into a user-controlled checkpoint, providing a much-needed layer of physical security.
Expanding Privacy with Advanced Browser Protection
Safari’s anti-fingerprinting technology now extends to all browsing modes, not just private sessions. This function blocks covert user tracking that relies on unique device and browser configurations to build invasive profiles of online behavior.
The real-world impact is a major boost to user privacy. It makes it significantly harder for websites and data brokers to monitor online activity across different sites, reducing exposure to the pervasive surveillance that defines much of the modern web.
Intelligent Filtering for Scams and Spam
The update enhances call and message filtering with real-time screening of unknown callers and automatic sorting of spam texts into a separate folder. This proactively isolates potential threats from the user’s immediate view, reducing digital clutter and risk.
These features mirror recent security trends in the Android ecosystem, indicating an industry-wide response to the rise of phishing scams and unwanted communications. This unified front helps create a safer mobile experience for everyone.
Recent Trends and Implementation Issues
This update reflects a broader industry trend where manufacturers like Apple, Google, and Samsung are tightening defenses against malicious data connections. This collective action highlights the seriousness of the physical hacking threat in today’s mobile landscape. However, the rollout has faced issues, with a bug causing some security settings to be “greyed out” for certain users. A fix is expected, but this currently prevents some from activating these vital new protections, representing a temporary gap in the defensive wall.
Practical Applications and User Scenarios
The update offers direct protection in real-world scenarios. For example, it allows travelers to safely use airport charging stations by enabling port protection, mitigating the “juice jacking” threat that the TSA has explicitly warned about. It also helps defend against sophisticated spyware attacks by limiting tracking vectors and reduces exposure to common phishing scams by filtering suspicious calls and texts before they can deceive the user, providing a multi-layered defense.
Adoption Hurdles and Mitigation Strategies
A primary hurdle is that critical protections, like the anti-juice jacking feature, are not enabled by default. This reliance on manual user intervention means many users may remain unprotected simply because they are unaware that action is needed.
Apple’s mitigation strategies involve patching bugs to ensure accessibility and potentially enhancing usability in the future. Making these settings more visible and easier to activate could encourage the widespread adoption needed for them to be truly effective.
The Future Trajectory of iPhone Security
The future of iOS security likely involves more integrated AI-driven threat detection to proactively counter new attacks. This could be coupled with deeper hardware-level security measures for a more holistic defense that adapts in real-time.
These advancements will continue to shape the balance between personal privacy and device safety. As a result, they will influence security standards across the entire mobile device industry, pushing all manufacturers toward more robust and intelligent protection.
Conclusion and Security Recommendations
This iOS update delivers crucial protections against physical hacking, browser tracking, and common scams. It provides users with essential, tangible tools to safeguard their digital lives against a range of modern and evolving threats.
The overall assessment is positive, and the recommendation is clear for all eligible users. It is imperative to install the update and immediately navigate to the settings to configure the new security features, as this is the only way to ensure maximum protection.