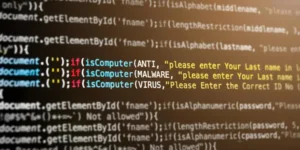
The emergence of remote code execution vulnerabilities such as CVE-2024-44236 presents an increasing challenge for macOS users worldwide. Recently uncovered by Hossein Lotfi of Trend Micro’s Zero Day Initiative, this vulnerability affects macOS versions Ventura 13.7, Sonoma 14.7, and Sequoia 15.1. To combat this threat, Apple rolled out updates on October 28, 2024. The vulnerability lies within the Scriptable Image