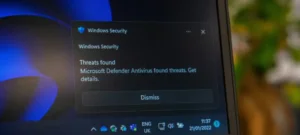
In a world where digital communication is integral to daily operations, cyber threats continue to proliferate with alarming sophistication and creativity. Among the most recent revelations is a novel technique employed by APT41, a group known for leveraging advanced tools and resources in cyber espionage. Their latest endeavor involves exploiting Google Calendar to hide malware, signaling a significant advancement in